Disk-Killer Malware Adds Ransomware Feature And Charges $200,000+
-

Talk about adding insult to injury with this new KillDisk version. Here is how social engineering can cost you dearly.
The Sandworm cybercrime gang has upped its game. They were initially named after the Sandworm malware which targeted and sabotaged Industrial Control Systems and Supervisory Control And Data Acquisition (SCADA) industrial devices in America during 2014,
The Sandworm gang later evolved into the TeleBots gang, which developed the TeleBots backdoor trojan, and the KillDisk disk-wiping malware.
KillDisk was used in 2015 and 2016 when another gang, the Russian BlackEnergy cyber-espionage group, used the malware to attack and sabotage energy- mining- and media companies in the Ukraine. Bad guys have very active forums and they talk all the time so this probably how state-sponsored Russian hackers got their hands on KillDisk.
Until today, the KillDisk malware strain was only active in espionage and sabotage ops. Well, they are now moving in the ransomware racket with a bang: 222 Bitcoins ransom, which with the skyrocketing Bitcoin exchange rate is well over 200 grand. If you get hit with this and your backups fail, that gets very expensive.
The new KillDisk strain uses very robust encryption, giving each file its own AES key, and then encrypting the AES key with a public RSA-1028 key. These guys know what they are doing.
KillDisk was recently used against Ukrainian banks
Recent KillDisk attacks were against Ukrainian banks. These attacks infected bank workers with the TeleBots backdoor trojan via phishing attacks with malicious email attachments. TeleBots is an easy to recognize malware strain because it uses the Telegram protocol to communicate with its criminal owners.
Catalin Cimpanu at Bleepingcomputer said: "After collecting data from infected systems, such as passwords and important files, the TeleBots gang would deploy the KillDisk component, which deleted crucial system files, replaced files, and rewrote file extensions. The purpose was to make the computer unbootable and also hide the intruder's tracks.
In the recent attacks against Ukrainian banks, the KillDisk malware had also been altered to use the Windows GDI (Graphics Device Interface) and draw a picture inspired by the Mr. Robot TV series, showing the logo of the FSociety hacktivism group, portrayed in the show.
At one point in the TV show, the FSociety group also infected the eCorp bank network with ransomware. The same is now true for the TeleBots gang, who added a ransomware component to KillDisk, as an alternative to disk-wiping operations."
Why did they add a ransomware feature?
It's easier to hide your tracks if KillDisk would pose as ransomware. You are basically talking a very profitable form of obfuscation.
The victim would assume they suffered an expensive ransomware infection, and wouldn't scan for the TeleBots trojan or other data exfiltration code. Victims trying to avoid bad PR would restore from backup or pay the ransom and move on. Meanwhile, back at the ranch they would still be robbed blind.
According to malware researchers at CyberX, the KillDisk ransomware component shows the following message on infected computers and asks for a huge ransom demand of 222 Bitcoin, well over 200 grand.
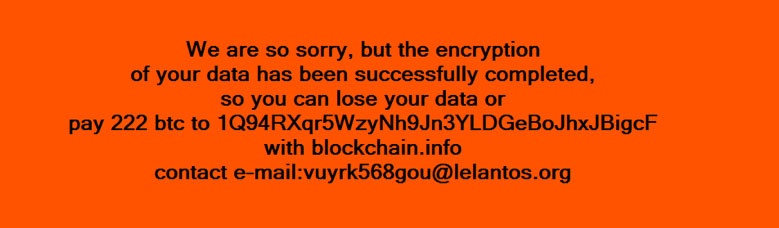
To unlock your files, you have to contact their customer support via an email and pay the ransom, and then receive your private RSA key that decrypts all your files.
The business model used here is not the spray-and-pray of the cheap ransomware. This gang goes for the high-end approach and demands a high price. Once you contact them through the email address, they will try to extort you threatening to dump sensitive files they stole via the TeleBots backdoor.
if you are not a KnowBe4 customer yet, at times like this, it is very good to know what percentage of your users are vulnerable to social engineering attacks. We recommend you do your free Phishing Security Test and find out what your phish-prone percentage of your users is.
https://info.knowbe4.com/phishing-security-test-16
Let's stay safe out there.
Warm regards,
Stu Sjouwerman
Founder and CEO, KnowBe4, Inc.















