Social Engineering Tactics: A Flow Chart
-
<article>
tl;dr
</article>
Mystery Sauce: http://www.smartfile.com/blog/social-engineering-attacks
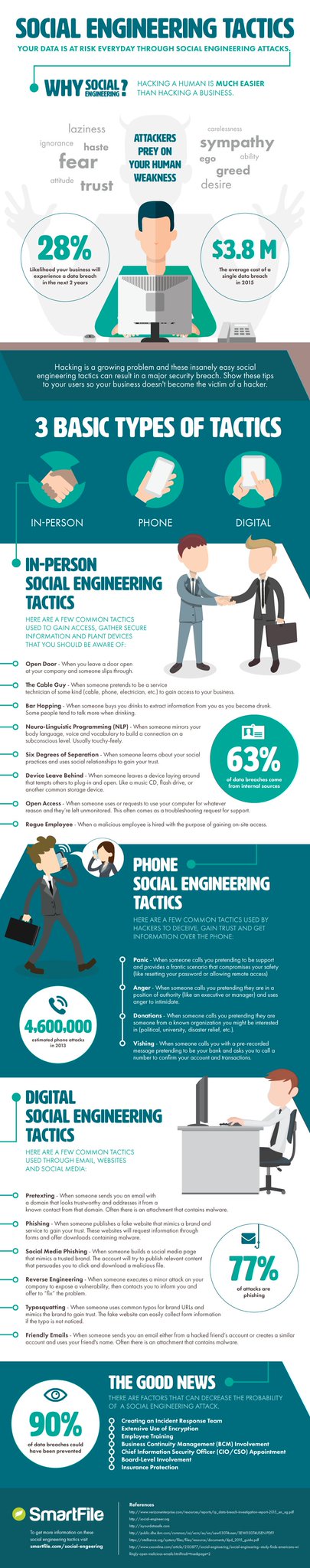
-
Hey, that's from SmartFile, we know those guys!
<article>
tl;dr
</article>
Mystery Sauce: http://www.smartfile.com/blog/social-engineering-attacks

Hey, that's from SmartFile, we know those guys!