Why Advanced Ransomeware Is Cybercrimes Most Profitable Business Model
-
https://blog.knowbe4.com/why-advanced-ransomware-is-cybercrimes-most-profitable-business-model @stus
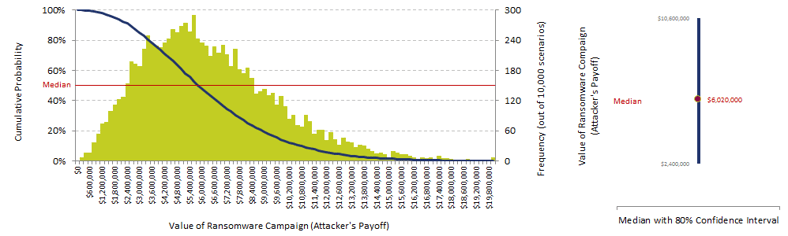
RSA did a revealing ransomware risk-reward analysis. See that $6 million number over to the right?
Why does cybercrime like ransomware so much? Low Risk, High Payoff
From the bad guy's perspective, advanced ransomware is highly lucrative with very little risk involved. The FBI estimates it will be a $1 Billion dollar 'business' in 2016. RSA did an analysis which gives us some insight in the money to be made!
"Assume, for instance, that a cybercriminal is targeting consumers and mounts an advanced ransomware campaign in which 1 million users are exposed to a fateful decision: to click or not to click. To be clear, this means several multiples of this number were launched—these are temptations that have successfully run the gauntlet of email security, Web security, and other preventive controls.
From this point, a simple Monte Carlo model quantifies the payoff from such a campaign:
- The probability of successful ransomware infection is between 0 percent and 10 percent, with a most likely value of around 4 percent.
- The victim’s willingness to pay ransom to recover his or her data is between 30 percent and 60 percent, with a most likely value of around 45 percent. Presumably, these users do not have a current backup of their valued data.
- The amount of ransom that victims are willing to pay is between $200 and $600, with a most likely value of around $300. Unsurprisingly, the Bitdefender study found that consumers place the highest value on their personal documents and photos and a lower value on work-related documents.
Using these assumptions, the math yields the following insights:
- The median payoff for an advanced ransomware campaign is about $6 million.
- The attacker has a 90 percent likelihood of a payoff greater than $2.5 million and a 10 percent likelihood of a payoff greater than $10.5 million.
The chart above combine this level of return with the significant reduction in risk provided by the use of Bitcoin for payment, and it’s easy to understand the growth in this criminal activity."
Ransomware Attacks On Corporations
For larger organizations, both for-profit and non-profits it gets a bit more complicated and also a lot more expensive. To start with, the damage caused by a ransomware infection is can be significantly higher due to several factors: downtime, ransom demanded, and fines by regulators related to the data breach.
Here Are 8 Things To Do About It (apart from having weapons-grade backup)
- From here on out with any ransomware infection, wipe the machine and re-image from bare metal
- If you have no Secure Email Gateway (SEG), get one that does URL filtering and make sure it's tuned correctly
- Make sure your endpoints are patched religiously, OS and 3rd Party Apps
- Make sure your endpoints and web-gateway have next-gen, frequently updated (a few hours or shorter) security layers
- Identify users that handle sensitive information and enforce some form of higher-trust authentication (like 2FA)
- Review your internal security Policies and Procedures, specifically related to financial transactions to prevent CEO Fraud
- Check your firewall configuration and make sure no criminal network traffic is allowed out
- Deploy new-school security awareness training, which includes social engineering via multiple channels, not just email